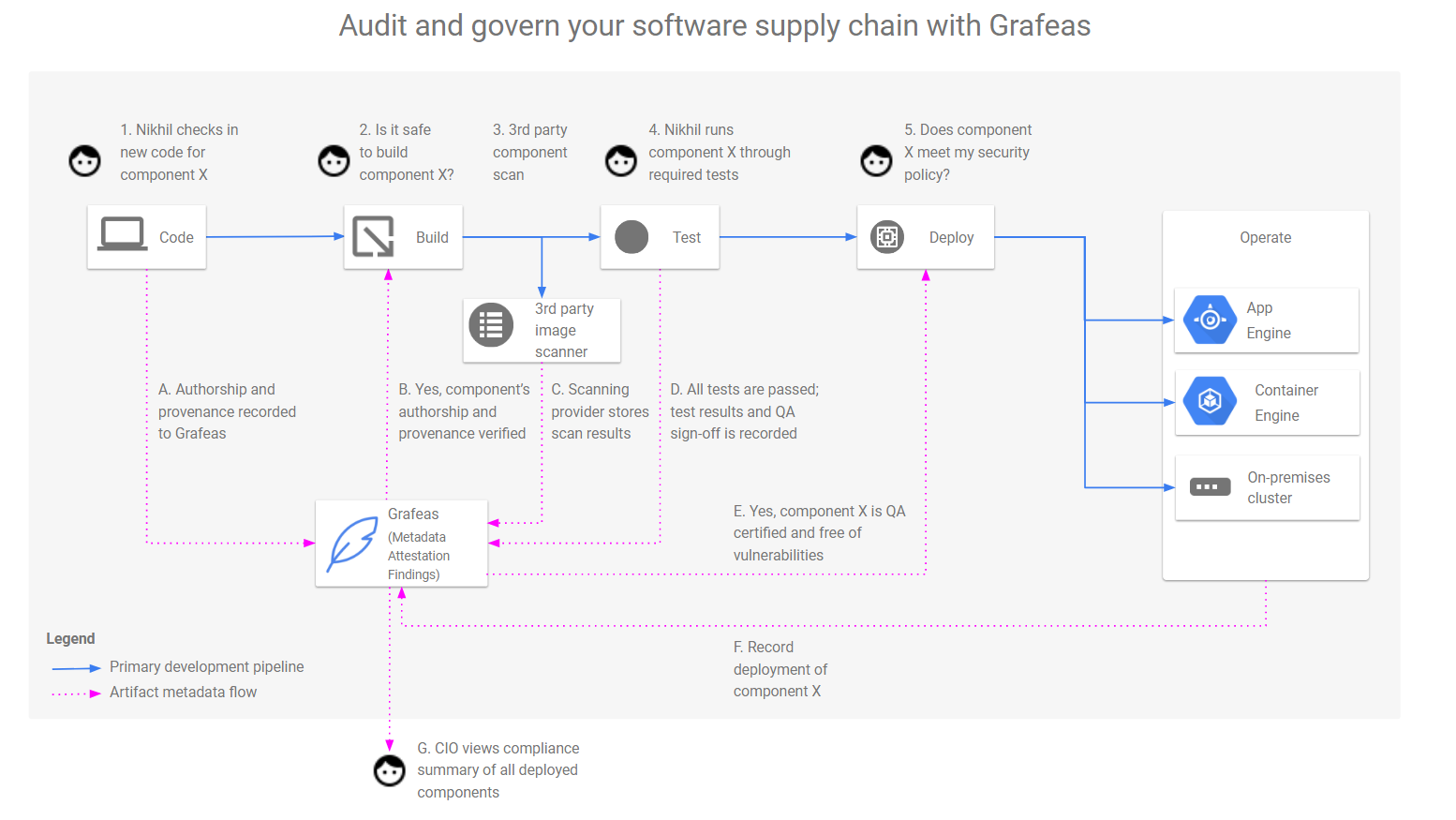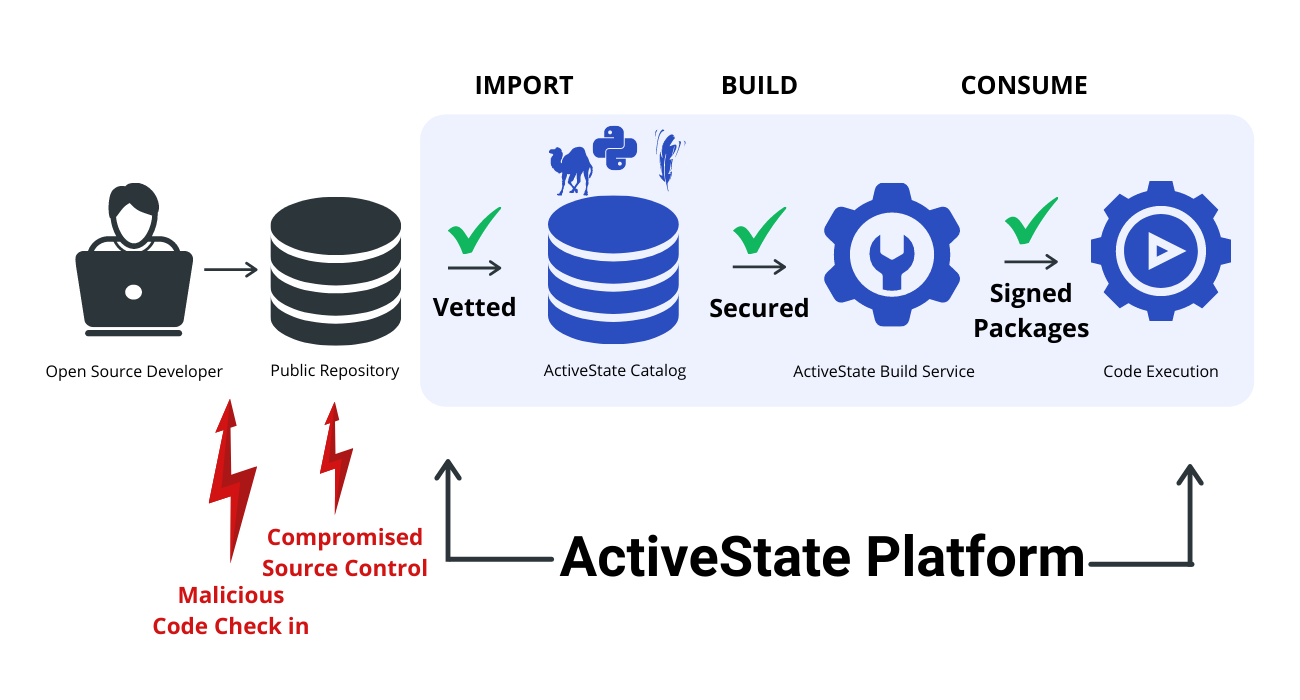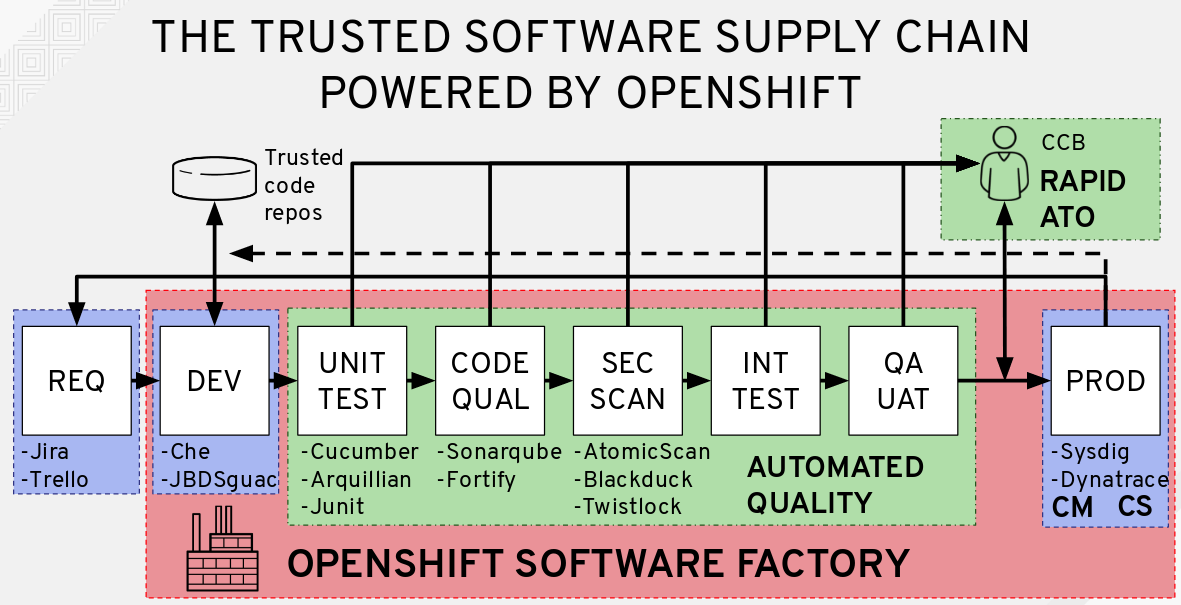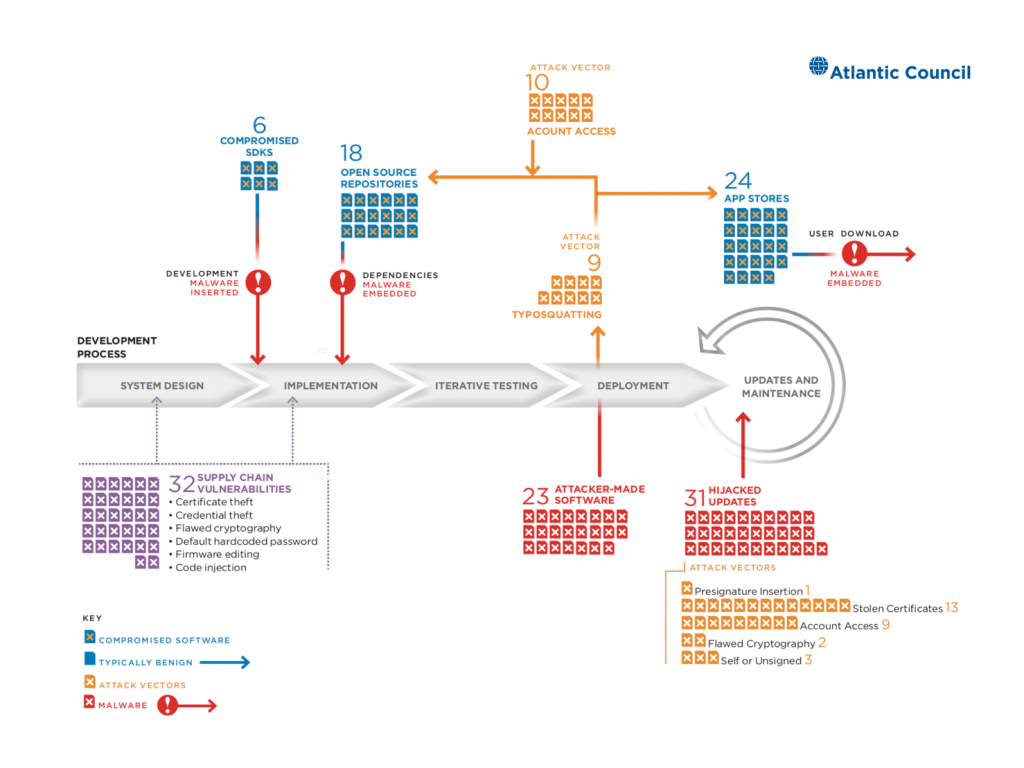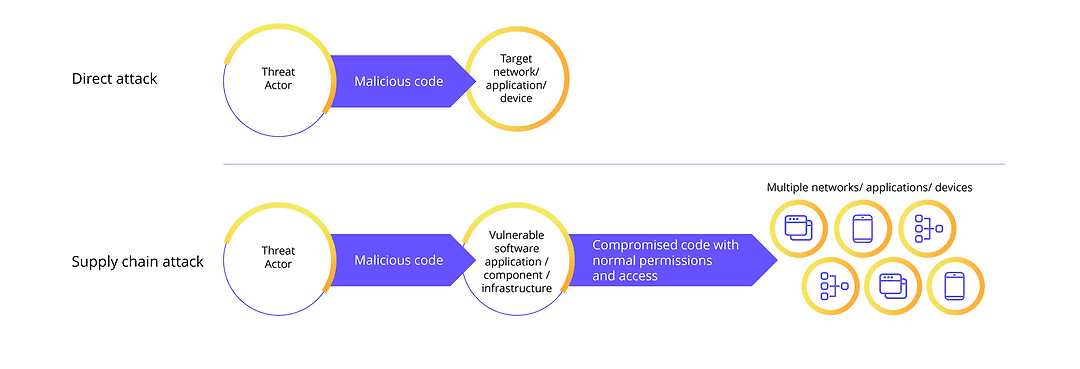
Software Supply Chain Security Ppt Powerpoint Presentation Show Picture Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

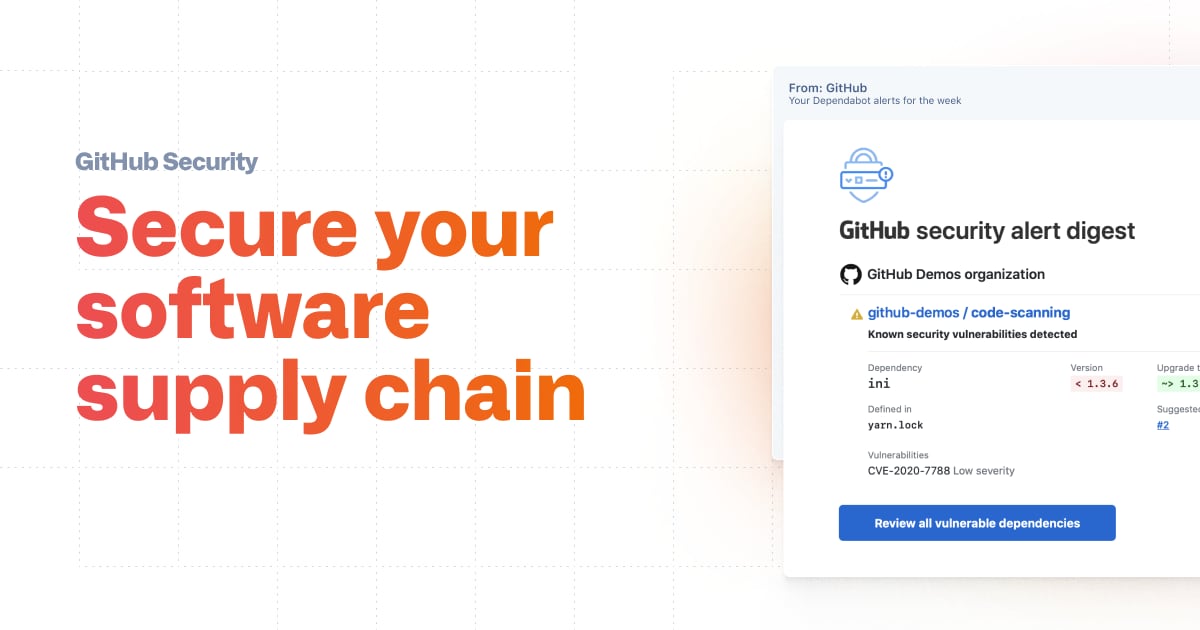
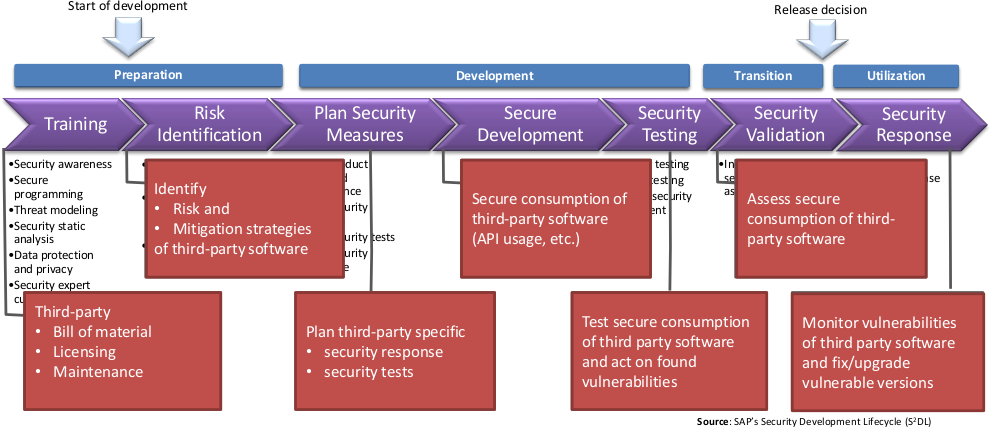
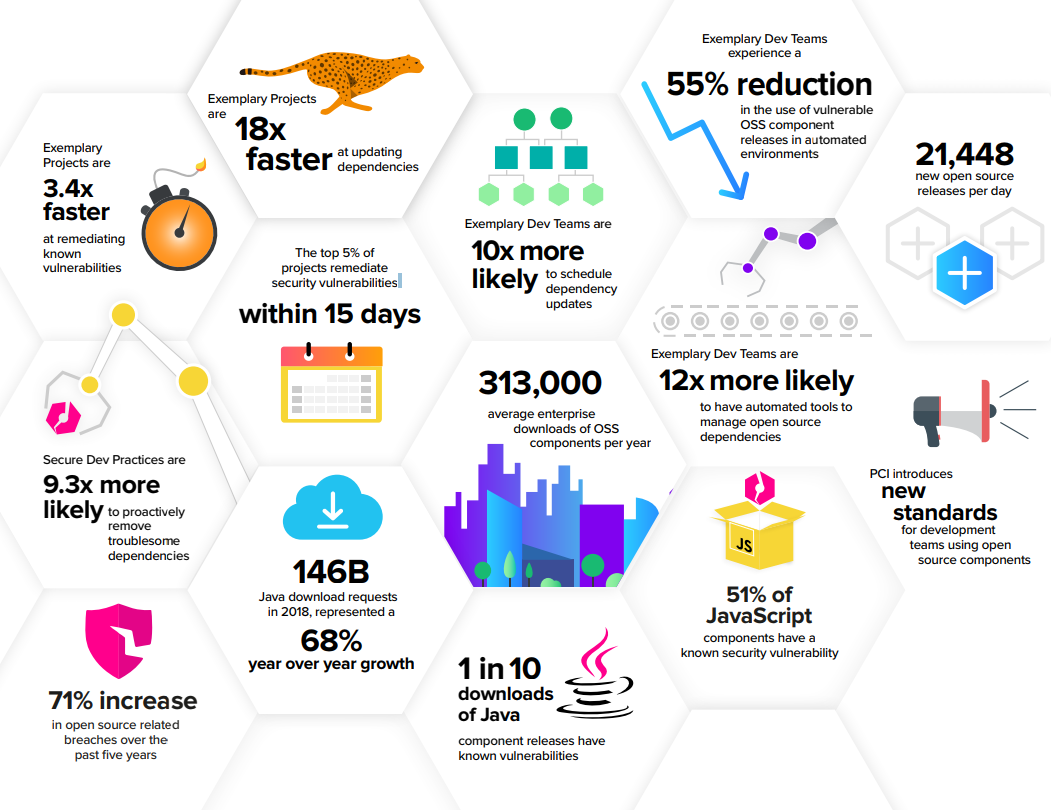
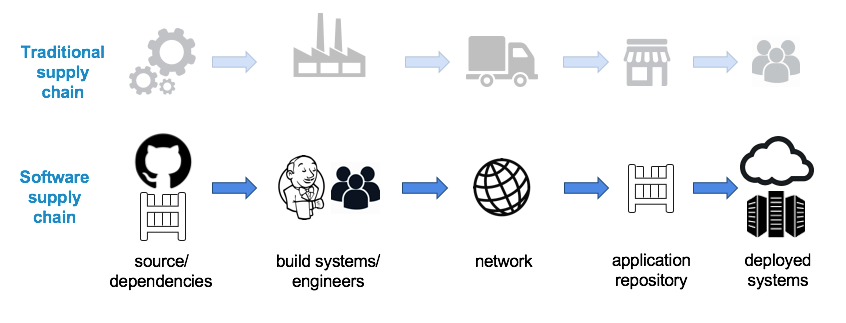
Secure at every step: What is software supply chain security and why does it matter? | The GitHub Blog