
Advisory: Two high-risk vulnerabilities in GoAhead web server - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
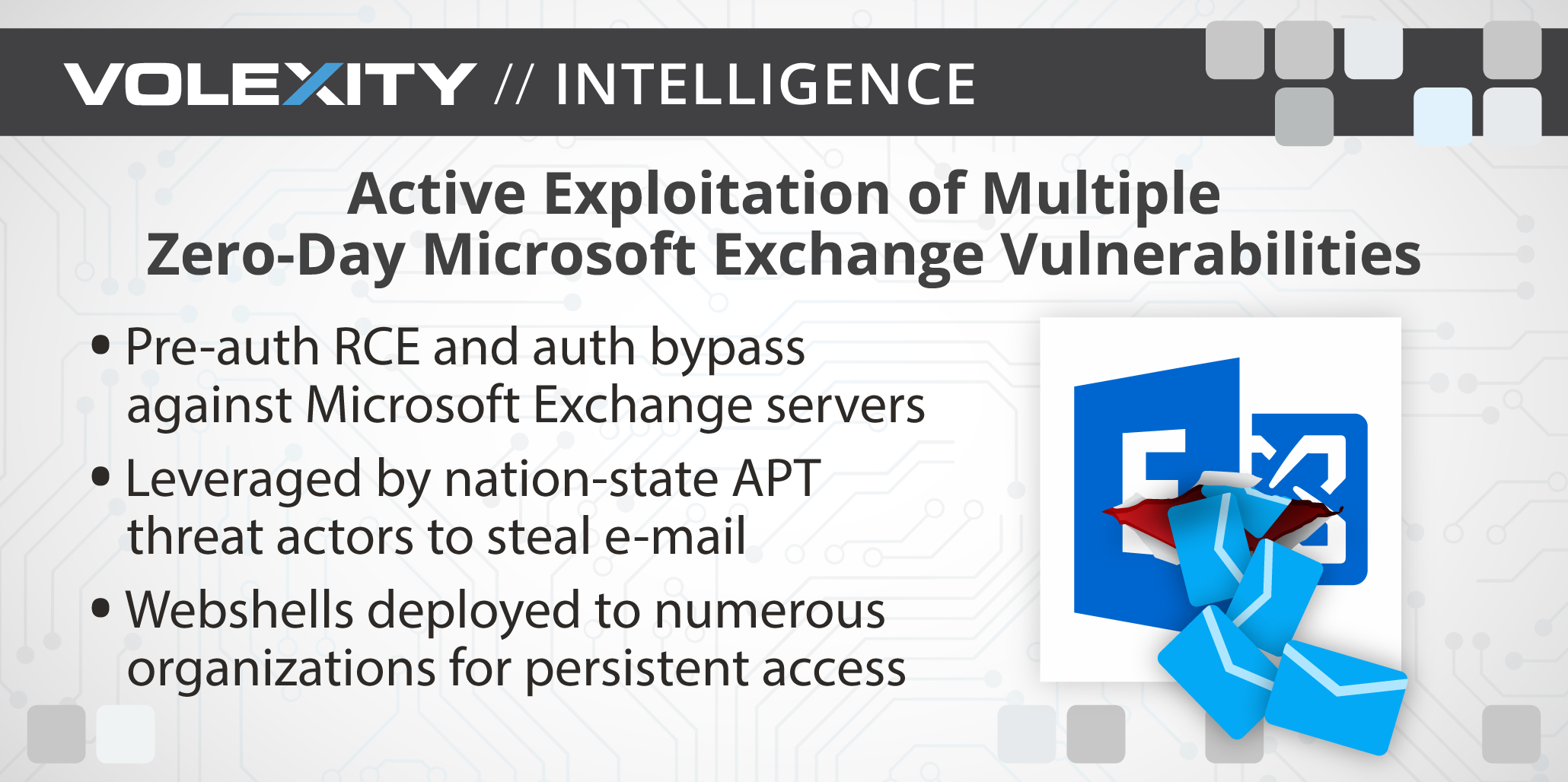
Operation Exchange Marauder: Active Exploitation of Multiple Zero-Day Microsoft Exchange Vulnerabilities | Volexity



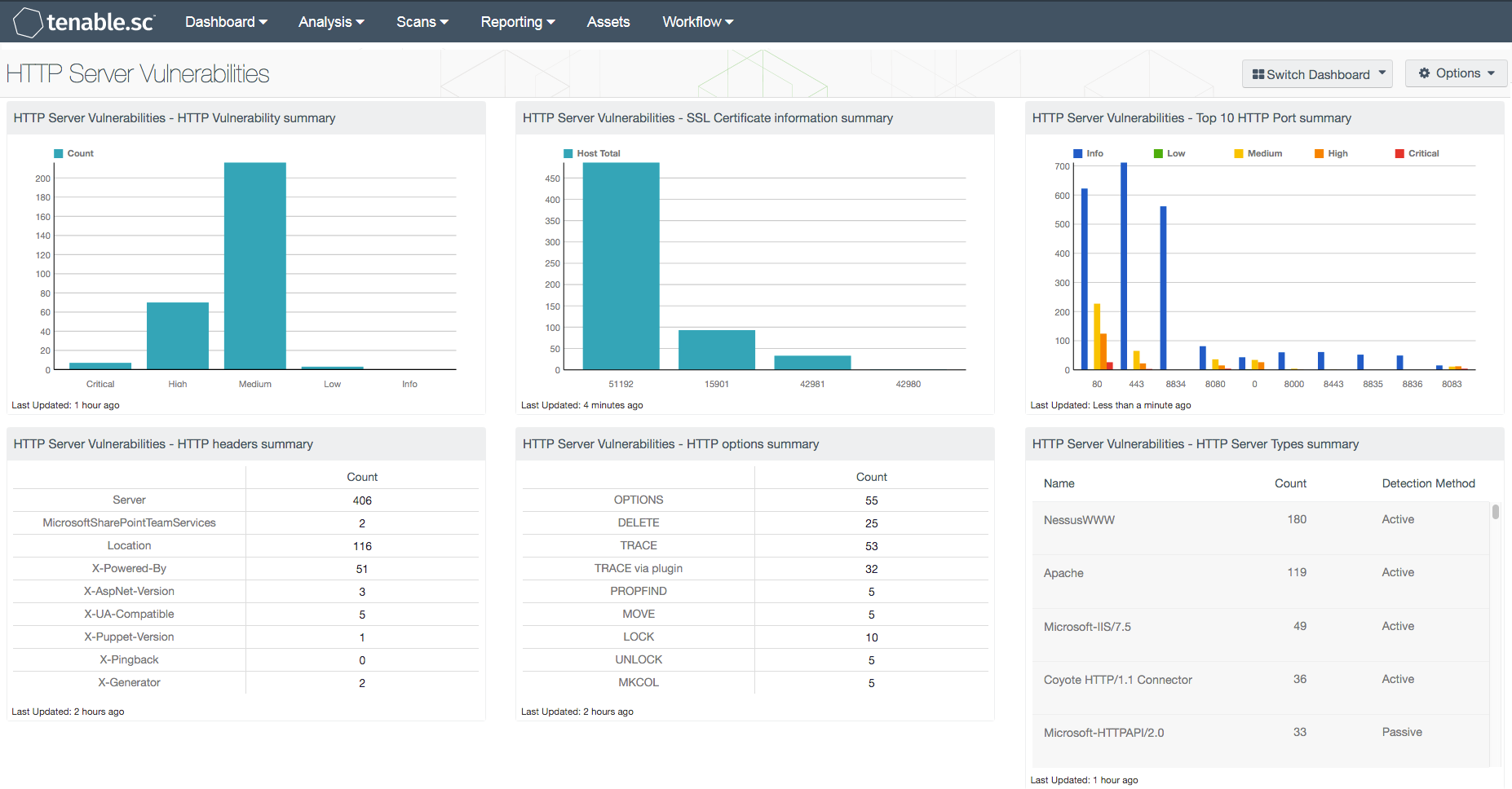











![Updated, again] Apache fixes zero-day vulnerability in HTTP Server | Malwarebytes Labs Updated, again] Apache fixes zero-day vulnerability in HTTP Server | Malwarebytes Labs](https://blog.malwarebytes.com/wp-content/uploads/2021/10/No_Access.png)





